Table of Contents
Introduction
Welcome to part one of ‘The Foundations of Digital Privacy’ series, where we delve into the core principles of securing your digital life. Unlike other setup guides, this series is designed to arm you with a comprehensive understanding of digital privacy that precedes technical application. This foundational knowledge serves as the critical first step on your journey toward a more secure and private online presence. In the next part, we’ll dive into the technical specifics of configuring pfSense for privacy enthusiasts.
Here. Take a cookie. I promise, by the time you’re done eating it, you’ll feel right as rain.
The Oracle
Like Neo in “The Matrix”, by the time you finish reading this blog post, you’ll walk away with a transformation of your own; the desire to adopt an always-on VPN with pfSense, integrate Unbound as your DNS resolver, and switch to Quad9 for DNS.
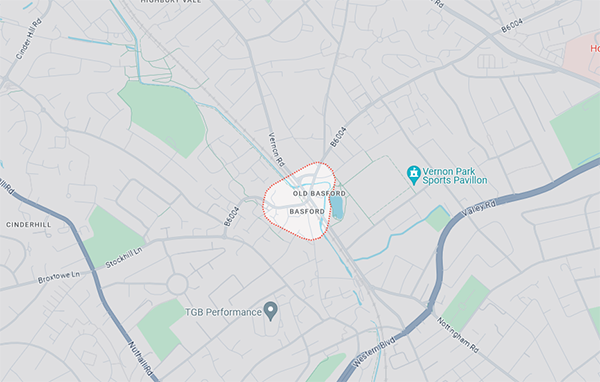
The motivation for this stems from a simple concern: the unsettling ease with which our online activities can be tracked and logged by virtually every website and service we interact with. Tracking that compiles a detailed record of our movements online, posing risks of exposure in data breaches or even through simple tools like whois lookups, which can reveal the approximate location tied to an IP address. The text below is from a whois lookup for an IP address based in the United Kingdom, showing just how accessible this information can be:
inetnum: 81.102.160.0 - 81.102.163.255
netname: VMCBBUK
descr: BASFORD
country: GB
admin-c: NNMC1-RIPE
tech-c: NNMC1-RIPE
status: ASSIGNED PA
mnt-by: AS5089-MNT
remarks: Virgin Media Consumer Broadband UK
remarks: Report Abuse via http://www.virginmedia.com/netreport
notify:
notify: Email Abuse & Blacklist & SPF contact <>
created: 2022-07-25T05:45:38Z
last-modified: 2022-07-25T05:45:38Z
source: RIPE
The IP address is allocated to a user in Basford, a small village in the United Kingdom. This allocation comes from a range designated for Virgin Media Consumer Broadband. Given Basford’s size, it significantly narrows down the potential location of the IP address to a few miles. While not all internet providers allocate their IP ranges similarly, Virgin Media’s approach demonstrates one method of assignment.
Digital Footprints
Consider the following: when you power on your Windows PC, Mac, or Linux machine, it begins to communicate with various online services. For instance, if you use Dropbox, the process associated with the Dropbox tray icon launches with your system’s startup, initiating communication with Dropbox’s cloud servers for data synchronization, update checks, and more. This activity, linked to your Dropbox account, is recorded along with your internet IP address. Your email address, username, and billing information are also associated with your identity, marking just one element of your digital footprint. The scenario extends to other applications that launch at startup, such as Adobe Creative Cloud, Microsoft Office, Firefox, and Google Chrome. Specifically, being logged into Google Chrome triggers background processes that communicate with Google’s cloud servers, capturing your IP, username, email, among other details, before you open the browser!
This illustrates why VPN client software alone is not sufficient for privacy. By the time the VPN service establishes a connection, even when it’s set to connect on start-up, your digital footprint had already begun to form with your real IP address. This extends to other devices on your network, including phones and gaming consoles, further expanding your digital trail.
VPNs Are Not For Anonymity
The amount of misinformation surrounding VPNs is staggering, potentially leaving newcomers to online privacy feeling overwhelmed and confused. To set the record straight:
VPNs do NOT provide anonymity.
When you route all of your online activities through a VPN tunnel, say to a server in New York, it appears as if all of your activities originate from that VPN server, and not your home internet connection. This means that instead of logging your real IP address, provided by your internet provider, these services log the IP address of the VPN server. Most reputable VPN providers claim to have a no logging policy, which means they do not keep records of your activities. However, they do ‘technically’ have the capability to enable logging. Should law enforcement or another government entity secure a court subpoena for your VPN provider (see here), they could compel the provider to start logging activities associated with your account. Thus, everything you conduct over the VPN could potentially be monitored and recorded.
For certain individuals, depending on their security concerns, this possibility represents a significant risk. However, it’s important to remember that anonymity is not the primary purpose of a VPN. For that, consider TOR.
So if VPNs don’t provide anonymity, then what are they for? Simply put, without one, your internet provider can monitor all of your browsing activity. That said, these days every service and site you access will very likely use HTTPS, so anyone snooping on your internet connection, such as your internet provider, won’t see the contents of your traffic, only what sites and services you visit. They can do this thanks to DNS, more on that in a moment.
Internet providers in Europe and other parts of the world have issued warnings to users about torrenting or pirating movies, music, and other activities. These warnings are part of efforts by ISPs to curb copyright infringement, following requests from copyright holders. For instance, users have reported receiving piracy warnings from their ISPs, which typically inform them that their internet connection was used to download and share copyrighted material. The notices detail the alleged infringement, including the time, date, and the content involved.
Companies like Warner Bros. have been involved in targeting file-sharers directly, even those using ISPs not participating in formal anti-piracy schemes like the Six Strikes in the United States. Warner Bros. and many other companies have been known to work with companies like Digital Rights Corp to send DMCA notices along with settlement offers to alleged infringers. These notices often include a payment option to settle alleged copyright infringements, effectively acting as a deterrent against future unauthorized sharing of copyrighted content.
This process does not require the ISP to monitor your browsing activity directly; instead, it relies on the visibility of your IP address in a public peer-to-peer (P2P) network. That’s why using a VPN can be crucial for privacy since a good VPN hides your real IP address and replaces it with one from their server, making it much harder for anyone monitoring a torrent swarm to trace activity back to you specifically.
Nothing to Hide
The “nothing to hide” argument is flawed because it fundamentally misunderstands the essence and importance of privacy. Privacy is not merely about concealing any wrongdoing; it is a core component of human dignity and autonomy. This argument assumes that privacy is only of concern to those who have something to hide, ignoring the fact that privacy rights enable individuals to control their personal information and protect themselves from potential abuses of power. It neglects the complexity of how personal data can be misused, irrespective of one’s innocence, such as for surveillance, identity theft, or unwarranted profiling. In a society where every action can be monitored, scrutinized, or taken out of context, individuals may self-censor or alter their behavior, not out of guilt, but out of fear.
If you give me six lines written by the hand of the most honest of men, I will find something in them which will hang him.
- Cardinal Richelieu
It’s also well-documented that many internet providers collect, sell, and even share user data, including browsing habits, with third parties. A report from the Federal Trade Commission (FTC) highlighted concerning practices among ISPs, such as collecting extensive personal and browsing data, grouping consumers using sensitive characteristics (e.g., race, sexual orientation), and sharing real-time location data with third parties. Despite some ISPs promising not to sell personal data, the report found that the data could still be monetized and used by affiliates, often hidden in the fine print of privacy policies.
Protecting our online privacy involves more than just using a VPN; DNS also plays a crucial role in this process.
DNS, The Right Way
The Domain Name System (DNS) is crucial to navigating the internet, even when using a VPN. Whenever you access a website, your device queries DNS to convert the domain name (like www.duckduckgo.com) into an IP address, which is necessary to connect to the desired web service. Routers supplied by your ISP will default to their own DNS servers, meaning DNS queries are managed by the ISP, which results in logging, analysis, and sharing of your online activities. So while nearly every website you visit now establishes an encrypted connection (HTTPS), your ISP will still know which sites you visited, when you visited them, your location, and they are doing this to sell (monetize) what you do on the internet.
Having established the importance of switching from the ISP-provided DNS server to enhance privacy, it’s worth noting that there are several reputable DNS providers available, such as NextDNS, OpenDNS, Cloudflare, and DNS.WATCH. Having experimented with each of them, I recommend Quad9.
Quad9 is a nonprofit organization based in Zurich, Switzerland, and receives funding from sponsors such as IBM, Packet Clearing House, and the Global Cyber Alliance. They ensure that no data containing your IP address is logged in any of the Quad9 systems and provide DNS encryption for enhanced privacy. Importantly, from a security standpoint, Quad9 offers the option of filtered DNS. This service, based on their threat feeds, blocks potentially malicious traffic from malware and other threats, adding an extra layer of security.
Do note, however, that if you switch from your ISP’s DNS to a service like Quad9, your ISP can still potentially see which websites you visit, but not through DNS queries. By using Quad9, your DNS queries are directed away from your ISP, thus preventing the ISP from logging these queries directly. Incorporating recursive DNS into the setup also adds an additional layer of obscurity. This is because resolving domain names through a process that traces the query back to the root DNS servers can make it more difficult for outside observers to track your specific browsing habits based on DNS queries alone. Later in this series, we’ll use Unbound to achieve this.
Nevertheless, unless your internet connection is encrypted through a VPN or similar technology, your ISP can still observe your internet traffic due to the inherent nature of how ISPs route internet packets. This raises an important question, ‘Is this sufficient?
DNS encryption
Since its inception, the Domain Name System (DNS) has traditionally utilized UDP port 53, a practice that continues to this day. However, the rise of digital surveillance and sophisticated cyber threats has necessitated the development of more secure methods of DNS querying. Encryption stands at the forefront of these efforts, offering a shield against prying eyes. DNS encryption techniques, such as DNS over HTTPS (DoH) and DNS over TLS (DoT), provide a crucial layer of security, ensuring that DNS queries and their responses are shielded from interception and manipulation. This not only enhances user privacy but also plays a significant role in the overall security of internet communications. Let’s delve into these encryption protocols and their implications for online privacy.
DNS over HTTPS (DoH)
DNS over HTTPS (DoH) represents a significant advancement in DNS query privacy and security. By utilizing the secure HTTPS protocol, DoH encrypts DNS queries and responses, effectively shielding this data from eavesdropping and manipulation by intermediaries. This encryption ensures that DNS traffic is indistinguishable from regular HTTPS traffic, complicating efforts by unauthorized parties to monitor which websites a user is attempting to access.
A key aspect of DoH is its use of HTTPS (specifically, TCP port 8443), which prevents governments and other intermediaries from monitoring or blocking DNS traffic. However, this has raised concerns among privacy-focused organizations, including Quad9. They caution that certain governments might escalate censorship efforts, potentially blocking all traffic not passing through their designated inspection proxies. Such actions could severely threaten internet freedom, indicating a move towards more controlled and monitored internet access.
DNS over TLS (DoT)
Transitioning to another layer of DNS security, DNS over TLS (DoT) offers a distinct approach to encrypting DNS queries. Unlike DoH, which integrates DNS queries within the broader HTTPS traffic, DoT encrypts DNS information through the Transport Layer Security (TLS) protocol. Operating on TCP port 853, DoT provides a robust encryption layer, protecting DNS requests and responses from being intercepted or altered.
The key distinction between DoH and DoT centers on their operational approaches and the specific ports they use. DoT is tailored to secure the DNS query process itself, without mingling it with other web traffic. However, the reliance on TCP port 853 could potentially make DoT traffic more detectable and subject to blocking by restrictive networks, which may limit its utility in environments with heavy internet censorship.
The choice between DoH and DoT will ultimately depend on the evolution of DNS security and the specific threat model you face. Factors such as your geographical location, the prevailing censorship and surveillance practices in your country, and the threats you encounter will significantly influence this decision. Remember, my focus is on ‘practical’ privacy, and simply using Quad9 DNS with a VPN might be more than sufficient for most. I just want to ensure you are aware that the topic extends beyond VPNs (hence the title!).
Encrypted Client Hello (ECH)
While we are discussing DNS encryption options, it’s important I mention the Encrypted Client Hello (ECH) extension for TLS. ECH enhances privacy by encrypting additional metadata that could be exposed during the TLS handshake. While both DoH and DoT encrypt DNS queries, ECH addresses a separate aspect of TLS communications, offering further protection by encrypting information that could reveal the specific website being accessed, beyond the DNS query itself. Confused yet? Don’t worry, I just wanted to mention it. If you want to read more about ECH, then check out this blog post.
If you are using Firefox version 118 or above AND using DoH, then ECH is enabled by default.
DNSSEC
DNSSEC (Domain Name System Security Extensions), isn’t about encryption, it’s about ensuring the integrity of data, a distinction often overlooked due to its name. Essentially, DNSSEC verifies that the digital signatures on DNS data, match, confirming that the data originates from its rightful source and remains unchanged during transit. DNSSEC may slow down DNS queries, although the impact is often minimal and depends on various factors including the resolver’s implementation and network conditions. It’s worth noting that Quad9 integrates DNSSEC validation within their recursive DNS process, alleviating the need to enable it in pfSense.
Unbound (Recursive DNS)
Alright, I’ve brought up Unbound already, so let’s dive into that a bit more. Unbound is a DNS resolver that sets itself apart from standard DNS servers by functioning primarily as a ‘recursive’ DNS resolver. Unlike traditional DNS servers, which often act as mere forwarders, sending your DNS queries up the chain to other servers until an answer is found, Unbound takes on the task of performing the full journey of a DNS query itself. This means it starts at the root DNS servers (.) and works its way down through the hierarchy of domain names until it locates the specific server hosting the DNS records for the domain you’re trying to reach (www.duckduckgo.com). This recursive approach not only enhances privacy by minimizing the number of servers that see your DNS queries but also improves security by directly validating DNSSEC signatures, ensuring the authenticity and integrity of the DNS data it retrieves.
By operating as a recursive DNS resolver, Unbound provides several key benefits over standard DNS servers. First and foremost; security.
You see, Unbound can effectively protect against DNS spoofing and cache poisoning attacks by verifying DNSSEC signatures, a level of security that is not inherently provided by many standard DNS services. Its ability to perform the entire name resolution process internally also means that Unbound can optimize DNS query paths for better performance, caching responses aggressively to speed up access to frequently visited domains.
Also, luckily for us, pfSense uses Unbound as the DNS resolver by default.
Note: I mentioned earlier that Quad9 already performs DNSSEC validation, which could alleviate the need to enable DNSSEC directly in pfSense. This is true. However, it’s important to understand that for you to fully benefit from Unbound’s DNSSEC validation capabilities (integrated within pfSense), DNSSEC must be explicitly enabled in pfSense. This ensures that DNSSEC validation occurs both externally (via Quad9) and internally (within your network).
Summary
Feeling right as rain yet? I’ve covered quite a bit, from the reality that VPNs aren’t a one-stop-shop for anonymity to wrapping our heads around DNS and its importance in keeping our digital lives private. Before we dive into setting up pfSense, I wanted to ensure you understand the rationale behind the ‘why’ of our approach. As you can now appreciate, it’s not as simple as going with whatever VPN
In part two, it’s time to roll up our sleeves and dive into the hands-on setup of pfSense. This is where we shift from theory to the fun stuff. We’ll walk through setting up that always-on VPN, getting Unbound to do the heavy lifting on DNS, and switching over to Quad9 for that extra layer of security. Then, I’ll show you how to run one or more VPN connections for an always-on VPN configuration with OpenVPN.
If you’ve actually read all of this and understood it, then give yourself a pat on the back! And if you’re now utterly confused, don’t worry! Just follow the steps in part two (coming soon), and it’ll all start to make sense.
See you soon!
